Deploy Firezone on GCP with Terraform
In this example, we will deploy one or more Firezone Gateways in a single VPC on Google Cloud Platform (GCP) that are configured to egress traffic through a single Cloud NAT that is assigned a single static IP address.
This example is built on top of our module for deploying a Firezone Gateway in Google Cloud.
Common use cases
Use this guide to give your Firezone Clients a static public IP address for egress traffic to particular Resource(s). Here are some common use cases for this example:
- Use IP whitelisting to access a third-party or partner application such as a client's DB or third-party API.
- Use IP whitelisting with your identity provider to lock down access to a public application.
- Enabling a team of remote contractors access to a regionally-locked application or service.
High availability
All Firezone Gateways deployed in this example will automatically failover and load balance for each other. No other configuration is necessary.
Prerequisites
- Terraform
- Google Cloud Platform (GCP) account
- Google Cloud SDK
- Enable the Compute Engine API
- A Firezone Site dedicated to use for this example. This Site should contain only the Firezone Gateway(s) deployed in this example and any associated Resources.
- A Firezone Gateway token. This can be obtained by viewing your Site in the
admin portal, clicking the
Deploy Gatewaybutton, and navigating to the instructions for theTerraformtab. Gateway tokens support multi-use, so only a single token is needed to provision the Firezone Gateways in this guide.
Sizing
Simply update the number of replicas to deploy more or fewer Firezone Gateways. There's no limit to the number of Firezone Gateways you can deploy in a single VPC.
If you need more than 64,512 concurrent connections, you can increase the number of public IP addresses reserved for the Cloud NAT. See Google's documentation for more information.
We've tested with e2-micro instances which still work quite well for most
applications. However, you may want to consider a larger instance type if you
have a high volume of traffic or lots of concurrent connections. See
Gateway sizing recommendations for
some general guidelines depending on your expected traffic.
Deployment
- Clone the module to your local machine:
git clone https://github.com/firezone/terraform-google-gateway
- cd into the
examples/nat-gatewaydirectory.
cd terraform-google-gateway/examples/nat-gateway
-
Configure the necessary Terraform variables. Here's an example
terraform.tfvarsyou can use as a starting point:project_id = "my-gcp-project" region = "us-west1" zone = "us-west1-a" token = "<YOUR GATEWAY TOKEN>" replicas = 3 machine_type = "f1-micro" log_level = "info" -
Run
terraform initto initialize the working directory and download the required providers. -
Run
terraform applyto deploy the Firezone Gateway(s) into your GCP project.
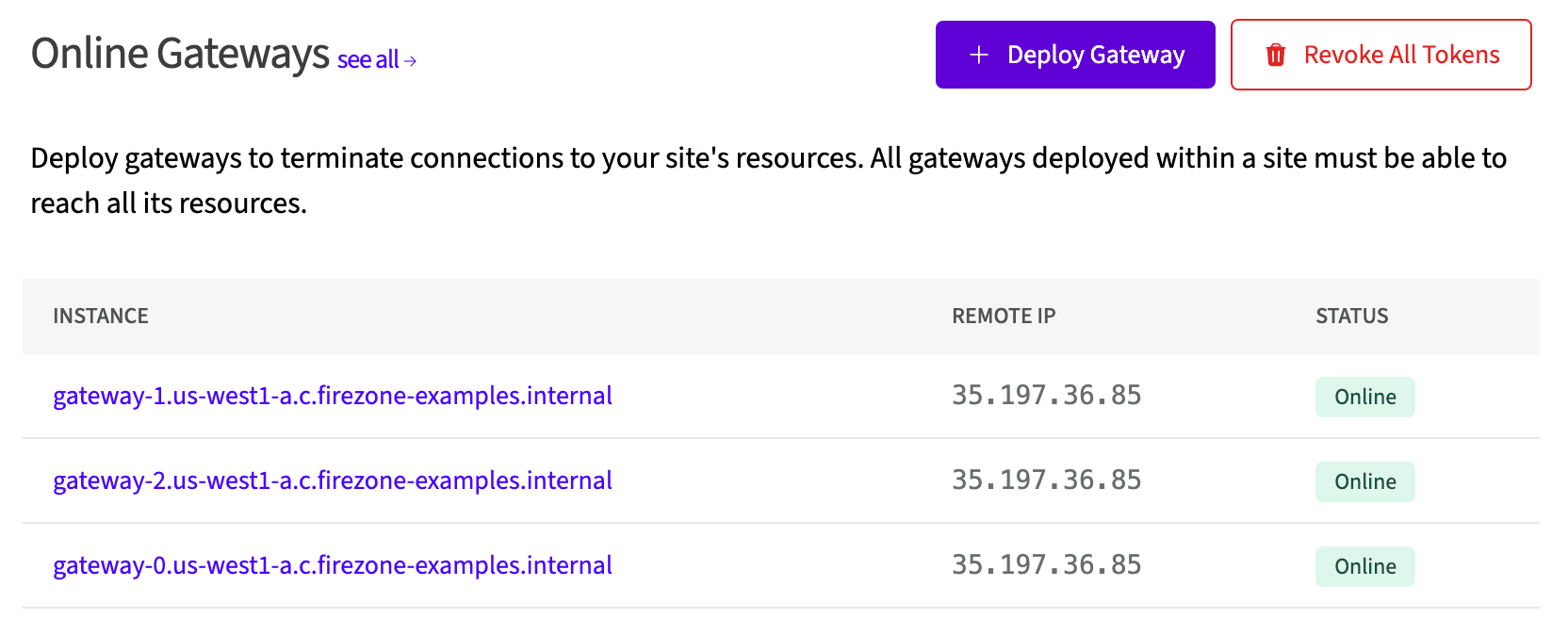
You can see the static IP address assigned to the Cloud NAT in the Terraform output. This is the IP address that your Firezone Gateway(s) will use to egress traffic.
You can verify all Firezone Gateways are using this IP by viewing the Site in
the Firezone admin portal, where you should now see the Firezone Gateway(s)
listed as Online.
It can sometimes take up to 30 minutes for all of the resources in this example to provision and connect to the portal. If you suspect the Gateway(s) are not connecting, follow the instructions in the troubleshooting guide to diagnose the issue.
Upgrading
To upgrade the Firezone Gateway(s) to the latest version, we recommend setting a
version to deploy with the vsn variable. Then, whenever you want to upgrade,
update this variable and run terraform apply, which will trigger a new
deployment of the Firezone Gateway(s) with the new version.
You can follow the latest releases of the Gateway at our changelog page.
This will incur a few minutes of downtime as Terraform destroys the existing Firezone Gateway(s) and deploys new ones in their place.
Output
static_ip_addresses will contain a list of static IP addresses that you can
use to whitelist your Firezone Gateway(s) in your third-party or partner
application.
Cleanup
To clean up the resources created by this example, run terraform destroy.