Access a Private Network
In this guide, we'll be using Firezone to secure access to a private subnet behind a firewall.
This is useful when you have hosts or services behind a firewall that you want to keep secure, but still need to access it from external networks like the internet.
In general, we recommend using a more granular approach to secure access using either DNS or IP-based Resources instead of the blanket approach used in this guide. Only use this guide if using DNS or IP-based Resources is not feasible, or if you need a stepping stone towards a more granular approach.
Prerequisites
- A Site that will contain the subnet you want to secure access to. Create a Site if you haven't already.
- One or more Gateways deployed within the Site. Deploy a Gateway if you don't have any in the Site where this subnet is located.
Opening ports on your network firewall is not necessary or recommended. Firezone Gateways perform secure NAT traversal for you.
Step 1: Create a Resource
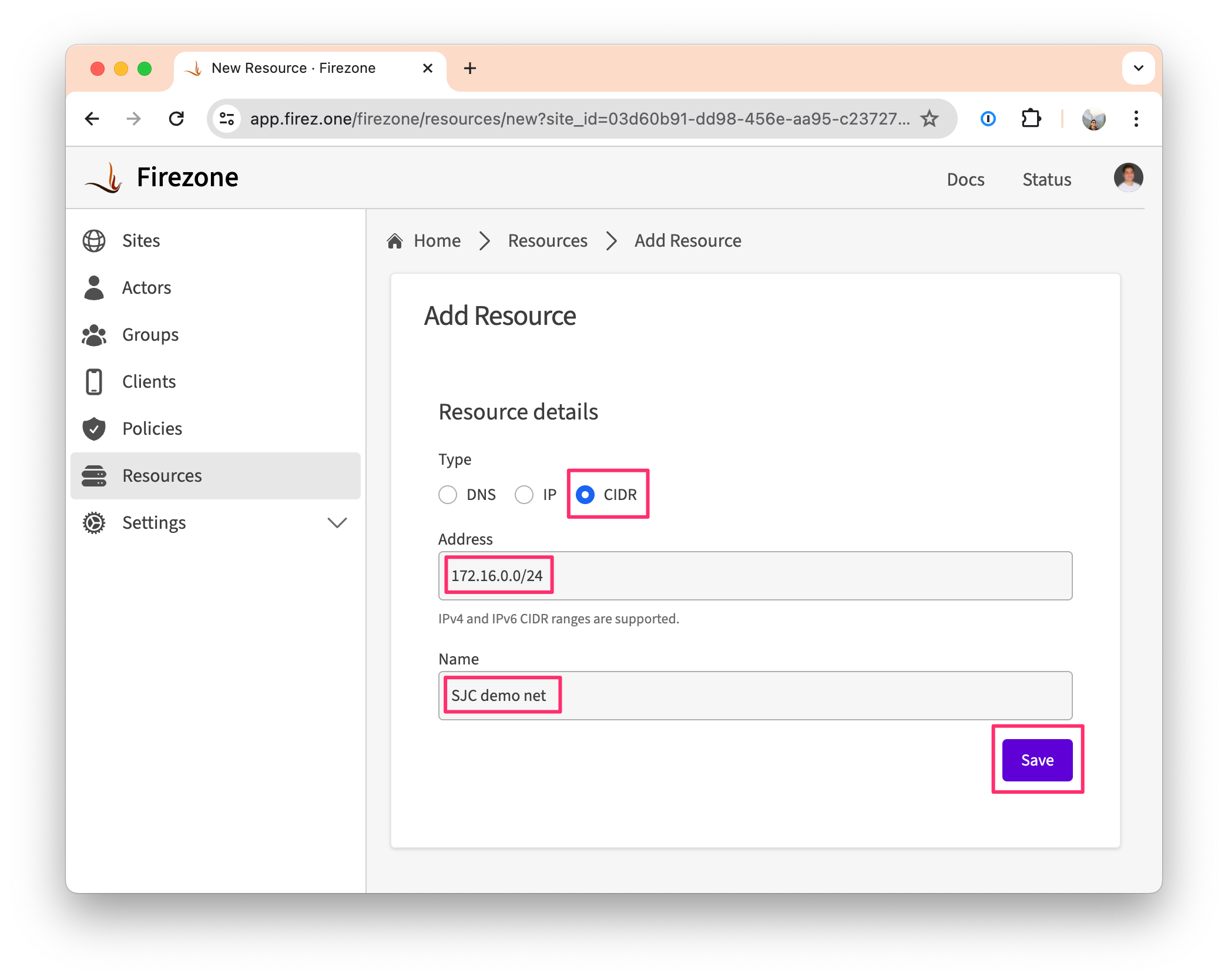
- In your admin portal, go to
Sites -> <site>and click theAdd Resourcebutton. - Select
CIDRas the Resource type. - Enter the CIDR range of the subnet you want to secure access to. This should be a range of IPv4 or IPv6 addresses that's directly reachable from the Gateway(s) in your Site.
- Name the Resource something descriptive, like
SJC demo net. You'll refer to this name when creating a Policy in the next step. - Click
Save.
Step 2: Create a Policy
- In the
Policiestab, click theAdd Policybutton. - Select an appropriate Group and the the Resource you created in Step (1).
- Click
Save.
Step 3: Done!
You should now be able to access hosts and services in the subnet you specified in Step (1).
Need additional help?
See all support options or try asking on one of our community-powered support channels:
- Discussion forums: Ask questions, report bugs, and suggest features.
- Discord server: Join discussions, meet other users, and chat with the Firezone team
- Email us: We read every message.