Manage Access to a SaaS Application
STARTERTEAMENTERPRISE
In this guide, we'll use Firezone to manage access to a public SaaS application such as HubSpot or GitHub.
This is useful when you want to restrict access to a public web app based on an IP allowlist configured in the app, effectively turning the Firezone Gateway into an app connector for SaaS applications that support IP allowlists.
Prerequisites
- A Site with a descriptive name to use for deploying Gateways for this use
case, for example
SaaS connectors. Create a Site if you haven't already. - One or more Gateways deployed within the Site in a NAT Gateway configuration. See Route traffic through a public IP for how to deploy a single NAT Gateway, or see our Terraform examples for examples on how to automate deploying multiple Gateways to various cloud providers.
- Any SaaS app that supports IP allowlists, configured to allow the public IP address(es) of the Gateway(s) you want to use.
For reliable access to your SaaS apps, we always recommend deploying multiple Gateways for high availability.
Step 1: Create a Resource
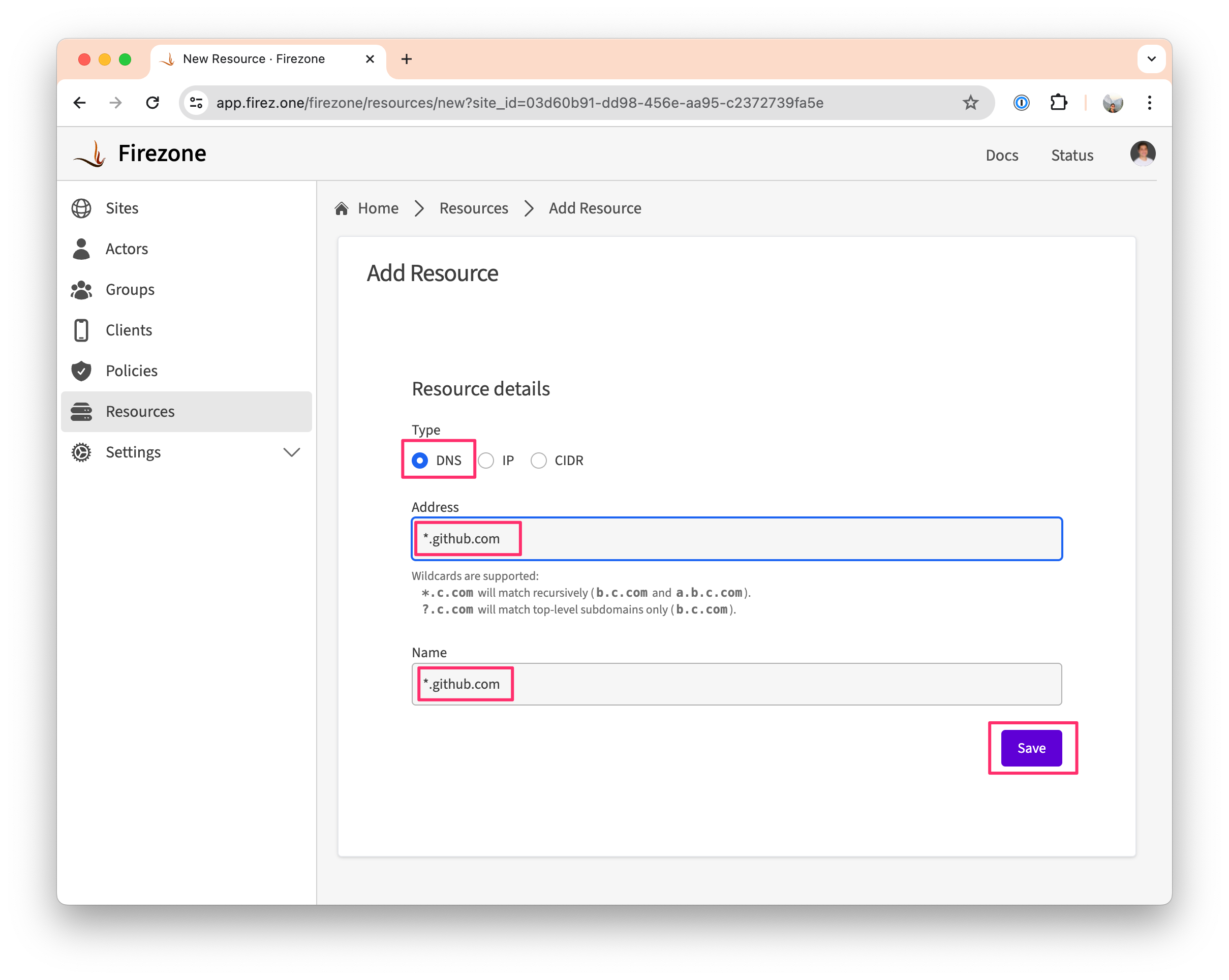
- In your admin portal, go to
Sites -> <site>and click theAdd Resourcebutton. - Select
DNSas the Resource type. - Enter the address of the SaaS app you want to secure access to. In some
cases, it's helpful to use wildcard matching to ensure all subdomains for the
SaaS app are routed appropriately as well. For example:
*.github.com. This address must be resolvable by all of the Gateway(s) in your Site. - Optionally, add a traffic restriction for
TCP/80and/orTCP/443to further limit access to this Resource to HTTP and/or HTTPS traffic only (Team and Enterprise plans). - Enter a descriptive name for the Resource, e.g.
Public GitHub access. This will be used to identify the Resource in the Firezone admin portal.
Step 2: Create a Policy
- In the
Policiestab, click theAdd Policybutton. - Create a Policy for the Resource you created in Step (1). Be sure to select the appropriate Group and Resource for the Policy.
Step 3: Done!
You've now secured access to your private web app with Firezone. You can now test access from any signed-in Client by visiting the SaaS app in a web browser.
Need additional help?
See all support options or try asking on one of our community-powered support channels:
- Discussion forums: Ask questions, report bugs, and suggest features.
- Discord server: Join discussions, meet other users, and chat with the Firezone team
- Email us: We read every message.
Or try searching the docs: