SSO with Fusion Auth
STARTERTEAMENTERPRISE
Firezone's universal OIDC connector has been tested to work successfully with Fusion Auth. Follow this guide to set up Fusion Auth for use with Firezone's OIDC connector.
Step 1: Create a new Application in Fusion Auth
- Within your Fusion Auth instance, click on the
Settingsmenu in the sidebar. Then selectKey Master.
- In the
Generatedrop down menu, selectGenerate RSA Key Pair.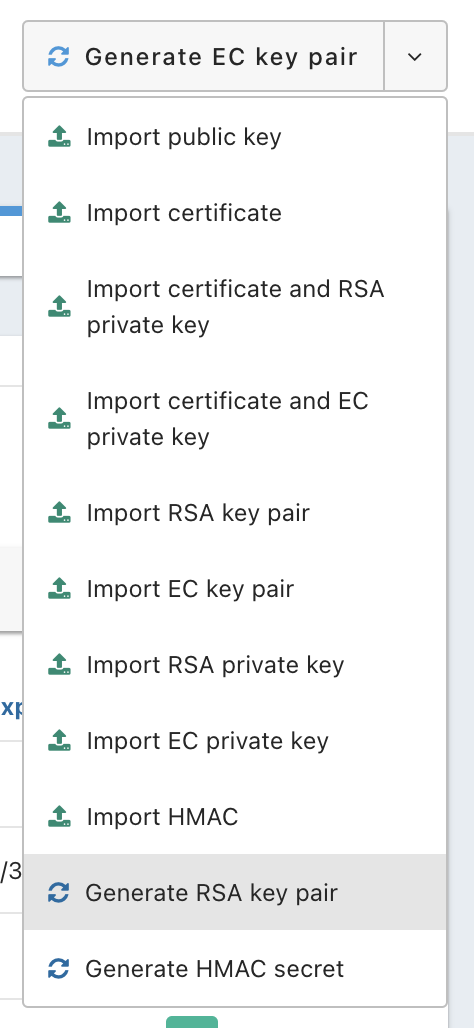
- Name the key appropriately, leave all other settings as their default.
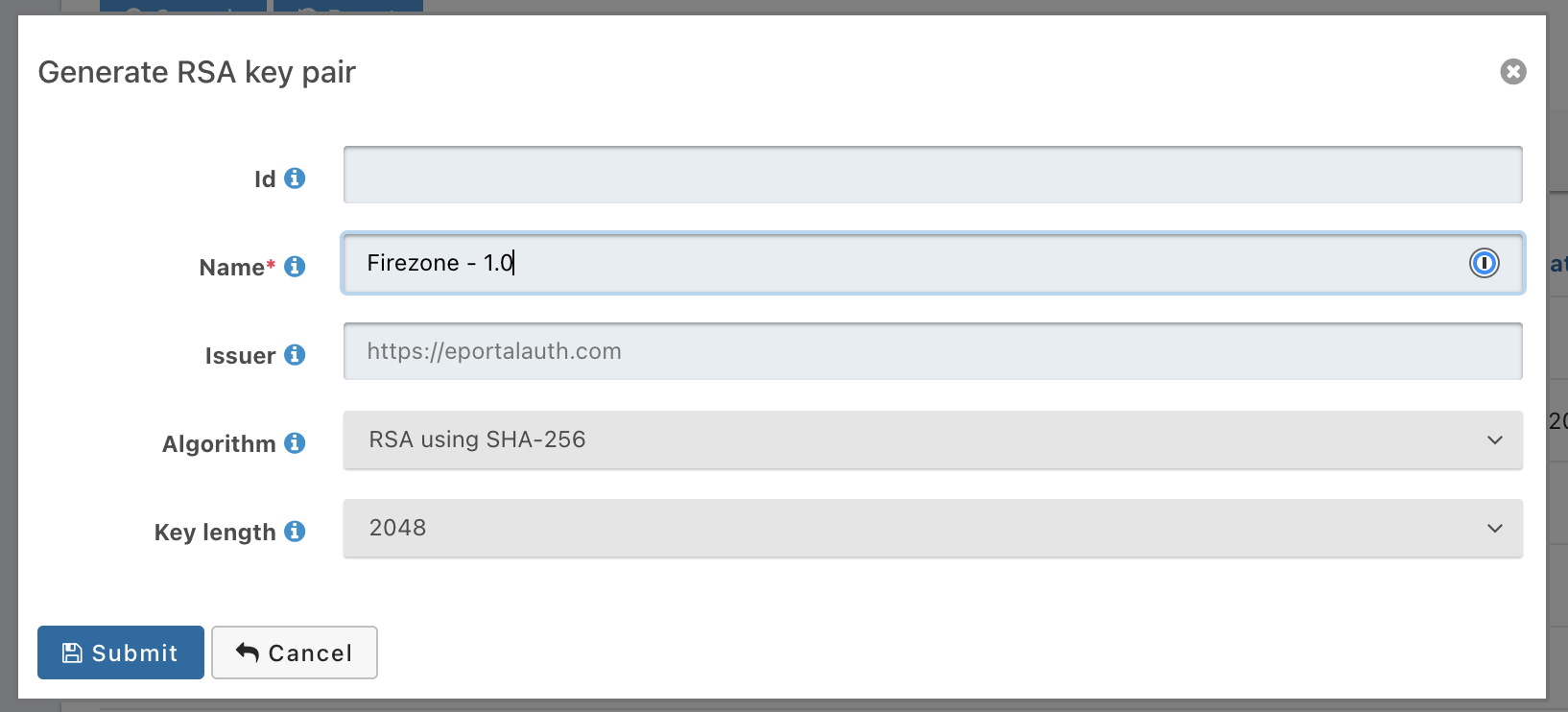
- Within your Fusion Auth instance, click on the
Applicationsmenu in the sidebar.
- Click the green + button at the top of the screen.

- Provide this application a unique name within your system (i.e.
Firezone-1.0). - Under the OAuth tab enter the two urls provided by Firezone in the Authorized
redirect URLs entry. Also add
https://app.firezone.devto the Authorized request origin URLs. You may enter any logout URL you wish. Optionally, enable PKCE for enhanced security.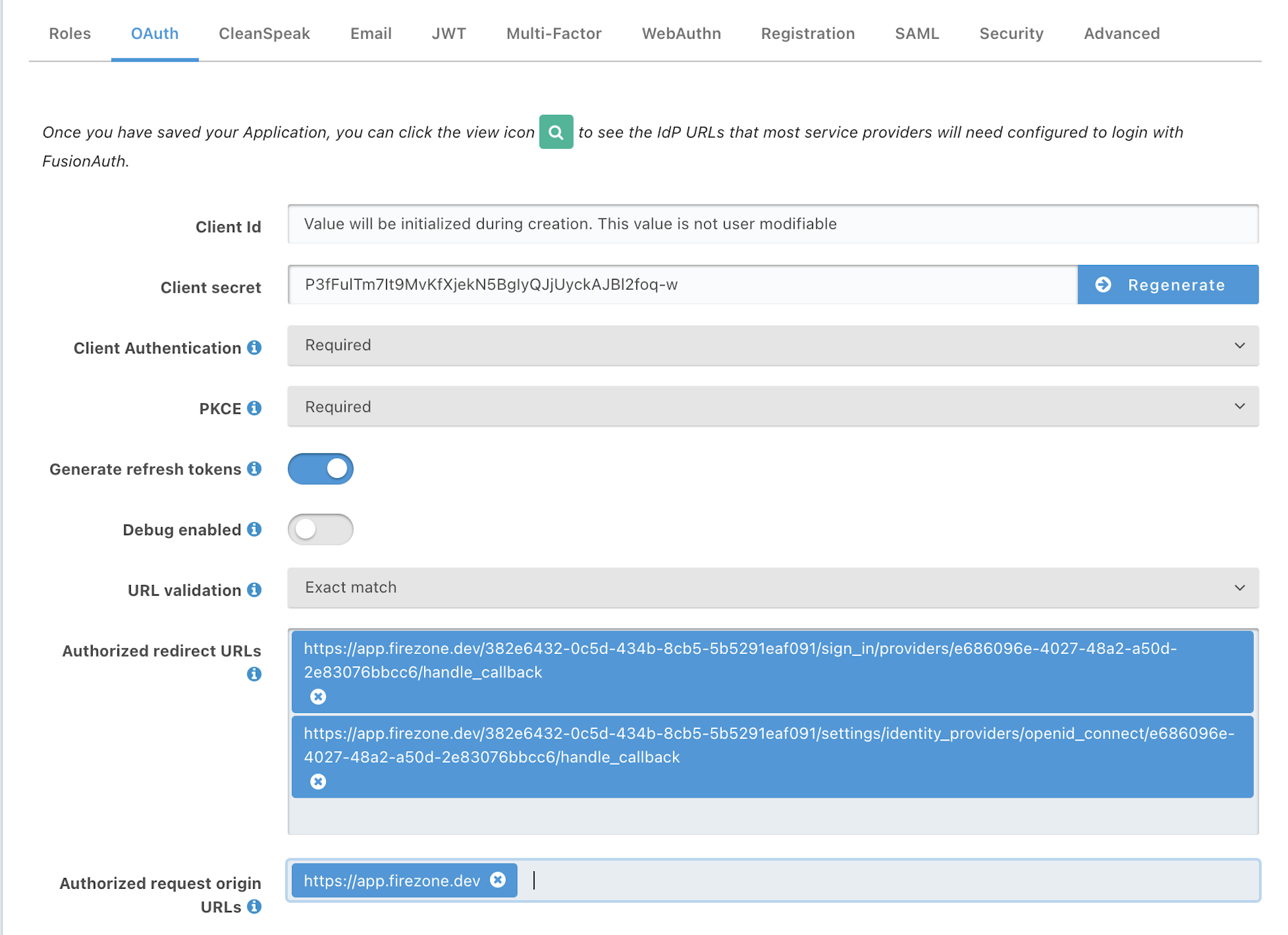
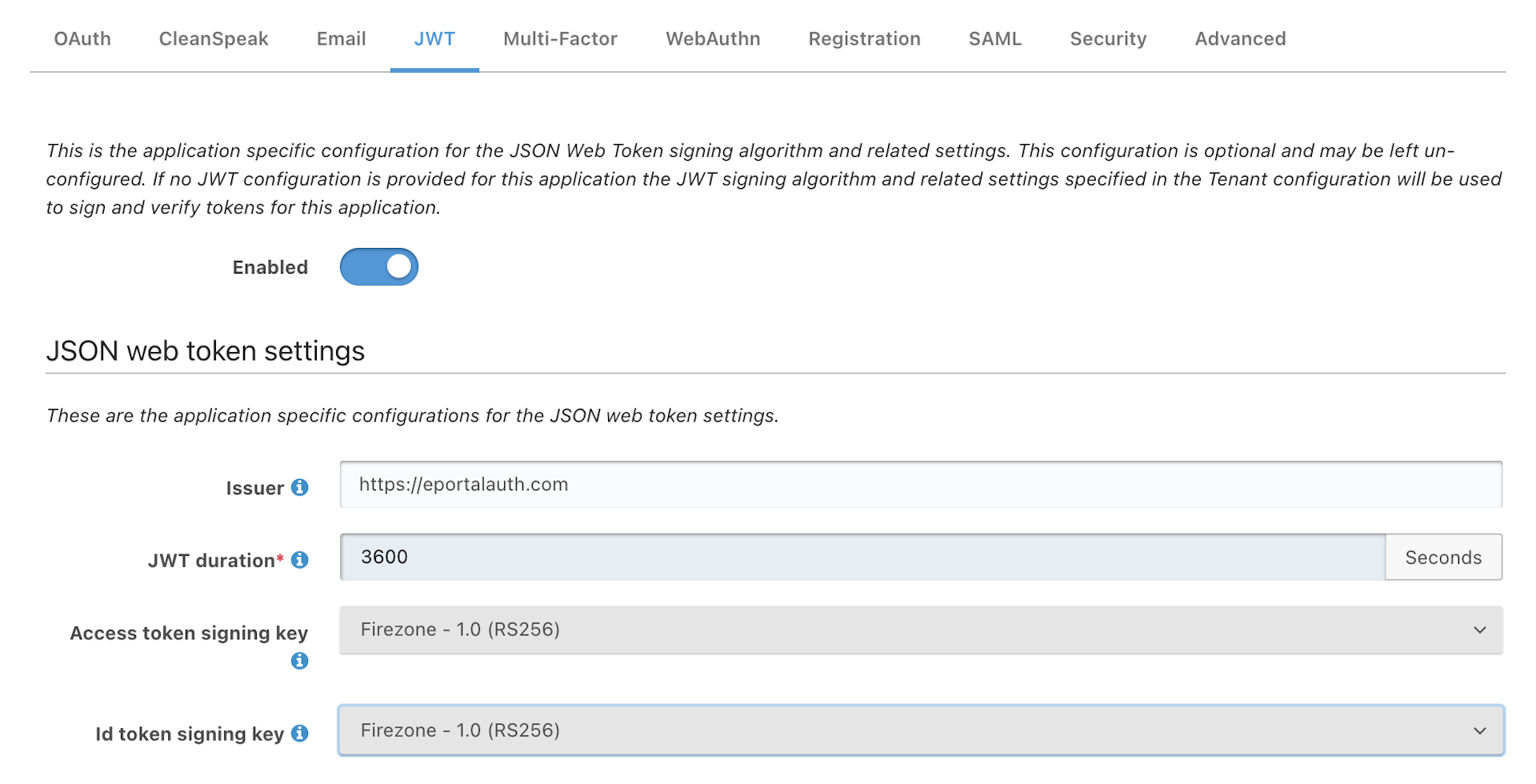
- Under the JWT tab, ensure that JWT is enabled. Also, for both entries under
JSON web token settings, ensure your newly created RSA key is used.
- Save your application. Then go back into your application in edit mode. Copy the client id / secret to enter into Firezone in the next step.
Step 2: Create identity provider in Firezone
- In your Firezone admin portal, go to
Settings -> Identity Providers -> Add -> OIDC. - Enter the
client idandclient secretsaved from the previous step. - In the Discovery URL, enter
https://<domain>/.well-known/openid-configurationreplacing<domain>with the domain you use to host Fusion Auth. - Click Create.
Step 3: Test
You should now be able authenticate users to Firezone using the identity provider just created.
Firezone does not automatically provision users or groups for identity providers using the universal OIDC connector. You must create Actors and associated Identities before the user will be able to sign in.
Need additional help?
See all support options or try asking on one of our community-powered support channels:
- Discussion forums: Ask questions, report bugs, and suggest features.
- Discord server: Join discussions, meet other users, and chat with the Firezone team
- Email us: We read every message.
Or try searching the docs: