Deploy Firezone on AWS with Terraform
In this guide, we'll deploy a cluster of Firezone Gateways in a private subnet on AWS that are configured to egress traffic to the internet through an AWS Internet Gateway.
Common use cases
Use this guide to give your Firezone Clients one or more public IP addresses for egress traffic to particular Resource(s). Here are some common use cases for this example:
- Access your AWS resources using more cost-effective, higher performance alternative to AWS Client VPN.
- Use an IP allowlist to access a third-party or partner application such as a client's DB or third-party API.
- Use an IP allowlist with your identity provider to lock down access to a public application.
- Enabling a team of remote contractors access to a regionally-locked application or service.
High availability
All Firezone Gateways deployed in this example will automatically failover and load balance for each other.
Prerequisites
- Terraform
- AWS account with the necessary permissions to create the resources.
- A Firezone Site dedicated to use for this example. This Site should contain only the Firezone Gateway(s) deployed in this example and any associated Resources.
- A Firezone Gateway token. This can be obtained by viewing your Site in the
admin portal, clicking the
Deploy Gatewaybutton, and navigating to the instructions for theTerraformtab. Gateway tokens support multi-use, so only a single token is needed to provision the Firezone Gateways in this guide.
Sizing
Simply update the number of desired_capacity to deploy more or fewer Firezone
Gateways. There's no limit to the number of Firezone Gateways you can deploy in
a single VPC.
We've tested with t3.nano instances which still work quite well for most
applications. However, you may want to consider a larger instance type if you
have a high volume of traffic or lots of concurrent connections. See
Gateway sizing recommendations for
some general guidelines depending on your expected traffic.
Deployment
- Download
the
main.tffrom the example module. - Customize it as desired. At a minimum, you will need to set the
firezone_tokenand changebase_amiandregionto match your environment. - Run
terraform initto initialize the working directory and download the required providers. - Run
terraform applyto deploy the Firezone Gateway(s) into your AWS project.
If your AWS VPC has restrictive Network ACLs in place, you will need to allow
UDP inbound traffic on ports 1024-65535 to allow connectivity from Firezone
Clients and Relays. For security groups, no inbound ports are required.
See our firewall recommendations for more
information.
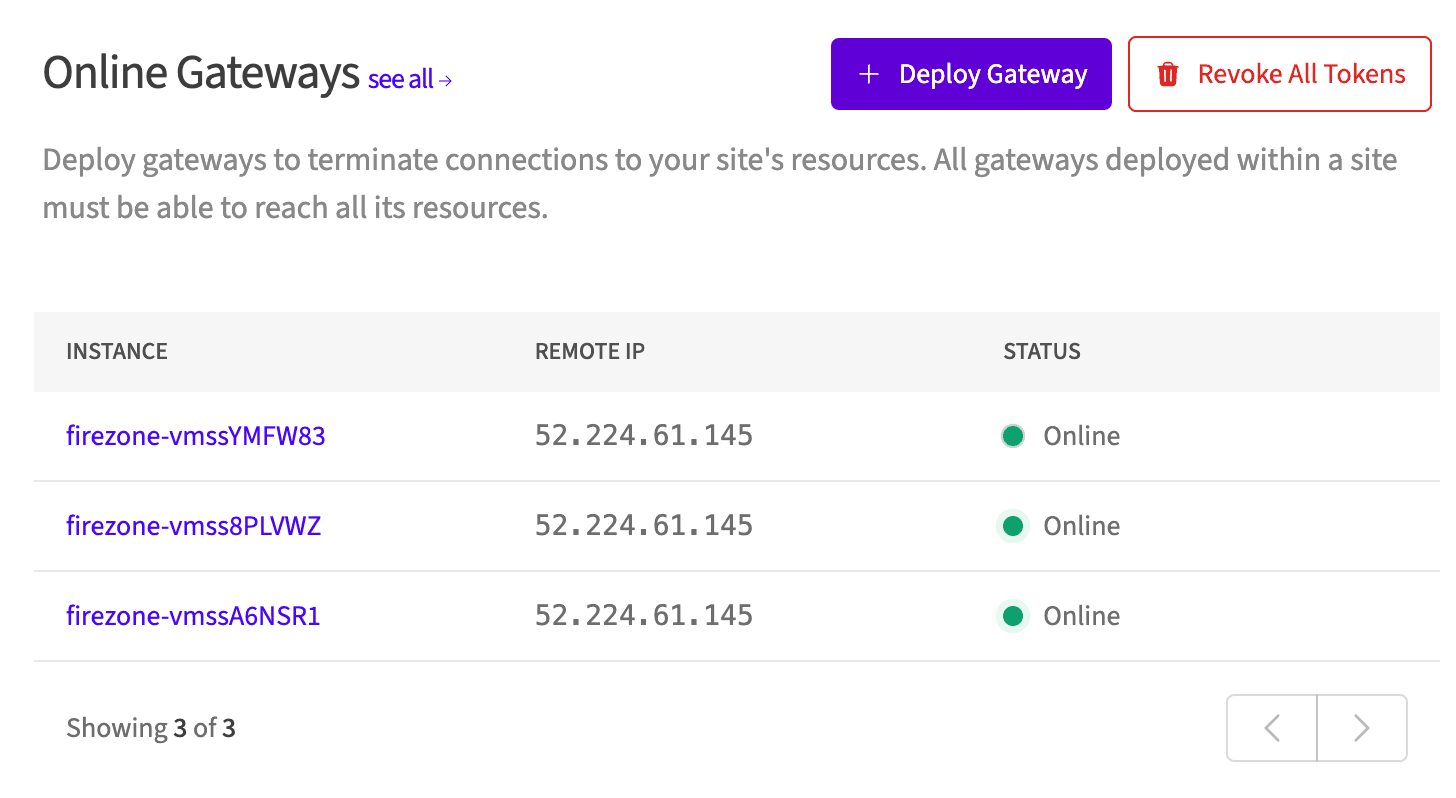
You can see the IP addresses assigned to the Gateway instances in the Terraform output. These are the IP addresses that your Firezone Gateway(s) will share to egress traffic.
These should match the IP addresses shown in the portal for the Gateway(s) you just provisioned:
It can sometimes take up to 30 minutes for all of the resources in this example to provision and connect to the portal. If you suspect the Gateway(s) are not connecting, follow the instructions in the troubleshooting guide to diagnose the issue.
After a few minutes, you should see the Firezone Gateway(s) appear in the Firezone admin portal. You can now configure your Resources to use the new Firezone Gateway(s) you just provisioned.
Upgrading
To upgrade the Firezone Gateway(s) to the latest version, we recommend setting a
version to deploy with the firezone_version variable. Then, whenever you want
to upgrade, update this variable and run terraform apply, which will trigger a
new deployment of the Firezone Gateway(s) with the new version.
You can follow the latest releases of the Gateway at our changelog page.
This will incur a few minutes of downtime as Terraform destroys the existing Firezone Gateway(s) and deploys new ones in their place.
Output
public_ips will contain the public Elastic IP address(es) you can use to
whitelist your Firezone Gateway(s) in your third-party or partner application.
Cleanup
To clean up the resources created by this example, run terraform destroy.
Need additional help?
See all support options or try asking on one of our community-powered support channels:
- Discussion forums: Ask questions, report bugs, and suggest features.
- Discord server: Join discussions, meet other users, and chat with the Firezone team
- Email us: We read every message.